Discussing Application Tier and its components can be very broad as it serves the business logic of the web application and all the services that it can support. But my intention of this blog is to provide a perspective of web application servers and the functionalities that supports.
In general term, the application Tier or middle Tier should take care of the application logic. And the technologies that are in place for application needs must be configured and integrated in application server. Among the services in this Tier are the HTTP service, session handling, distributing naming and lookup, database access, persistence, transaction management, caching, concurrency, messaging, security, and much more.
Looking back we had an EJB container that was taking care of the different beans (Session Bean, Entity Bean, and Message Bean) moving forward spring framework is in place for taking care of the middle Tier functionalities Spring IOC Container can accomplish the job.
As Java EE is still a major reference point, but it is not the only target. A promising framework technology for modular architecture is spring which its layered architecture allows you to be selective about which component you use while also providing a consistent framework for J2EE application development.
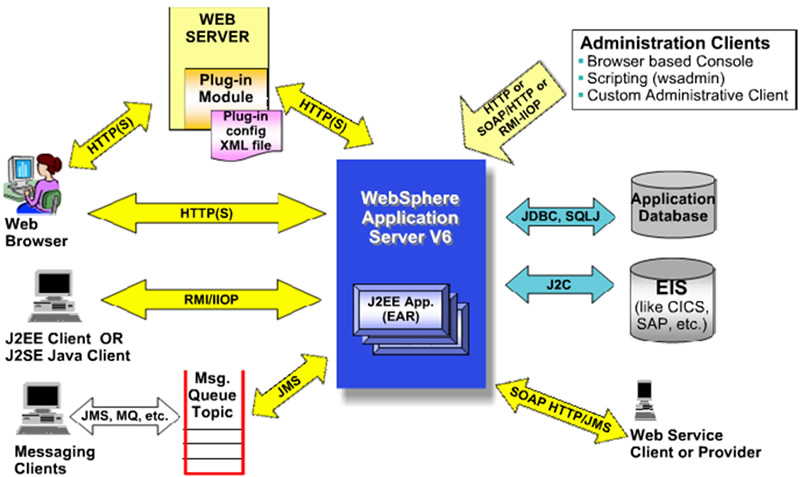
In this Tier, we need to have an Enterprise Application Server, like Oracle Weblogic Server, or Websphere Application Server from IBM. The following diagram is showing the flow of how clients make a request to a websphere application server and from the server to Enterprise Information Systems or databases or webservices.
The flow will be very similar to what you see in this diagram as in any other application server. As you see, either a web browser, J2EE Client or a messaging client will initiate a request through the protocol that suits each and going through the web server if it is required the requests will be sent to application server and eventually call the business logic method to achieve the requests and if there is a need to gather some data, the request will make the appropriate call to the Data Tier and respond with the correct information to the client.
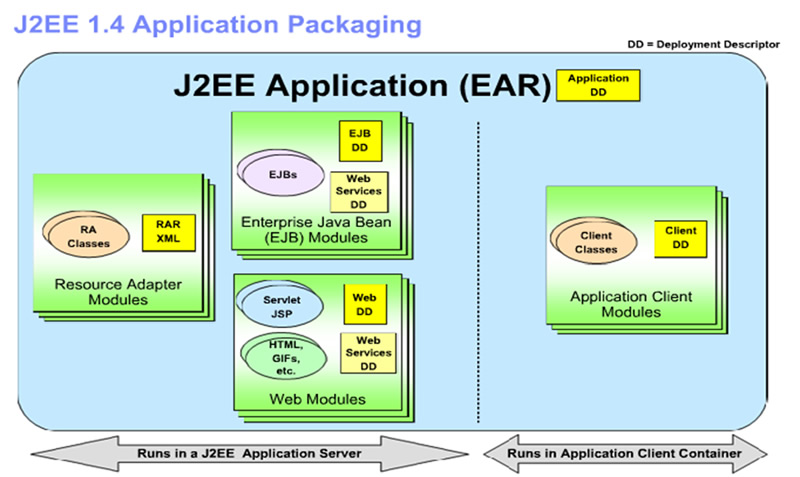
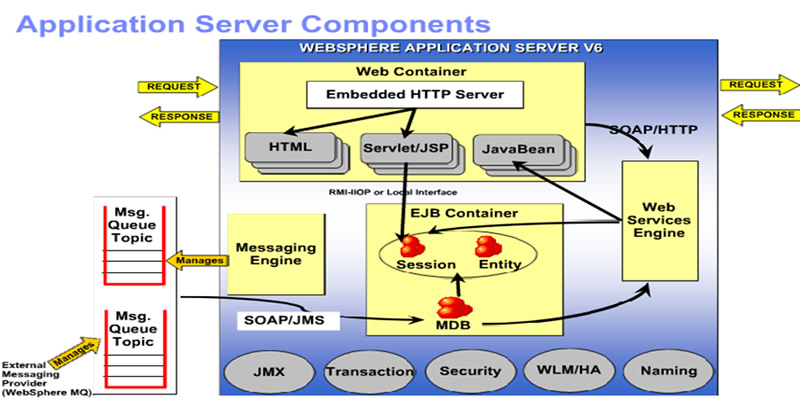
The following diagram is displaying the relation of Java EE application components, and application server components.
In any case though, the functionalities that need to be taken care of at this Tier are:
Session management, Resource management, Transaction management, Integration management, Enterprise Java Beans and Persistence management, Security Management,
Caching, Clustering, High Availability Management, Web Services integration and Interoperability Management, Integration and Messaging, Java Mail.
Most of these functionalities are taken care of via Application Server of choice; here are the websphere components that got designed to address most of the targets at this Tier.
In summary, for any sort of enterprise application development in application Tier, you need to choose the application server that you need to run your services on and also an architecture framework for implementing your modules.
Spring is the de-facto standard in lightweight enterprise application framework which is an open source. And as I mentioned Weblogic and Websphere are both among the industry’s leading application servers for building and deploying Enterprise JavaEE application. And another well-known application server is JBoss Enterprise Application Platform that is the leader in enterprise open source software.
All of these application servers are designed to operate in a distributed environment, and you can design a clustered environment running an instance of each if it is required over the distributed network. They have also capability of webservices design and development. Security is one the most important aspect to consider when planning for system architecture. All of them have different ways to enforce security all across the application from connection level through Secure Sockets Layer(SSL), at the application level through application specific policy constraints, and at the serve level through restriction access to a particular service, firewalls and so on.